Startup Roundup #2
Previously: Startup Roundup #1.
This is my periodic grab bag coverage of various issues surrounding startups, especially but not exclusively tech-and-VC style startups, that apply over the longer term.
I always want to emphasize up front that startups are good and you should do one.
Equity and skin in the game are where it is at. Building something people want is where it is at. This is true both for a startup that raises venture capital, and also creating an ordinary business. The expected value is all around off the charts.
That does not mean it is the best thing to do.
One must go in with eyes open to facts such as these:
-
It is hard.
-
There are many reasons it might not be for you.
-
There are also lots of other things also worth doing.
-
If you care largely about existential risk and lowering the probability of everyone dying from AI, a startup is not the obvious natural fit for that cause.
-
The ecosystem is in large part a hive of scum and villainy and horrible epistemics.
I warn of a lot of things. The bottom line still remains that if you are debating between a conventional approach of going to school or getting a regular job, versus starting a business? If it is at all close? I would start the business every time.
Deedy: HUGE Immigration News for International Entrepreneurs!!
If you own 10%+ of a US startup entity founded <5yrs ago with $264k+ of [qualified investments from qualified investors], you+spouses of up to 3 co-founders can come work in the US for 2.5yrs with renewal to 5yrs.
Startups globally can now come build in SF!
A “qualified investor” has to be a US citizen or PR who has made $600-650k in prior investments with 2+ startups creating 5+ jobs or generating $530k revenue growing 20% YoY.
If you don’t meet the funding requirement, don’t lose hope. You CAN provide alternate evidence.
For the renewal to 5yrs, you need to maintain 5% ownership, create 5+ jobs and reach $530k+ revenue growing 20% YoY or $530k+ in investment, although alternative criteria can be used.
While on the International Entrepreneur Rule (IER) program, I believe an entrepreneur can just apply directly for an O-1 to have a more renewable work permit not tied to their startup and/or an EB-1A to directly go to a green card.
Here is the official rule for it. Notice that once someone is a ‘qualified investor’ in this sense, their investments become a lot more valuable to such companies. So there is a lot of incentive to get a win-win deal.
If you are in AI, it’s time to build. Everyone wants to invest in you.
If you are not, times are tough for startups. Ian Rountree lays out exactly how tough.
Matt Truck: Brace for it: hearing from big companies corp dev departments that they’re flooded with requests of startups looking for a home. In some categories, pretty much all companies are/would be up for sale. This too shall pass but this long-predicted tough moment seems to be upon us.
Ian Rountree (late 2023): ’ve been saving my first mega-tweet for this! I’ll tell you what the next 3-12 months will probably look like for startups/venture…
But 1st let’s rewind to Spring 2022. As soon as rates spiked we had a period where private markets went flat for as long as companies had runway since companies don’t have to price their shares unless they like the price OR need the money. (Whereas liquid assets repriced pretty much immediately.)
Very few startups outside of AI—and some in climate and defense—liked the prices they were being offered so most didn’t raise capital or raised extensions from insiders incentivized to hold prices steady.
Now most startups are running out of the money they raised in 2020-2021 + those extensions so they’re forced to raise.
The great startups are raising mostly on flat rounds or slight up rounds—which is a big win when your public comps have faced multiple compression but no startup CEO I know will admit this publicly. They may kick and scream but they’re smart enough to face the music. That’s been happening the last couple months and it’s felt good as a VC. At @cantos we’ve seen 7-8 term sheets in our portfolio since September 1st. We’ve been calling it BOBA for “bounce off the bottom autumn”. (Feel free to steal that.)
But now WINTER IS COMING. The startups that can’t raise this Fall, probably the majority, will soon start failing and the headlines will NOT be pretty. It will look like an absolute bloodbath next year. Some may even claim venture is over, that this whole startup thing was a fad.
Here’s the thing though: this is all just a very slow ripple effect of rising rates that started ~18 months ago. These coming bankruptcies will be a LAGGING indicator. As inflated valuations come down (Google “multiple compression” if that triggered you) and VCs write many positions off, LPs will likely get MORE active (no longer held back by their denominator problem) and it will probably be a GREAT time to invest in startups or start a brand new company.
So when those headlines get published in the coming months fear not; be “greedy” instead. Painful as these failures will be—we’ll feel those in our portfolio viscerally, to be sure—it will be an inevitable, foreseeable, and ultimately healthy reset.
VCs always talk like this. Always it is a good time to start a new company, the great ones will make it, whatever we are offering you will work out, and so on.
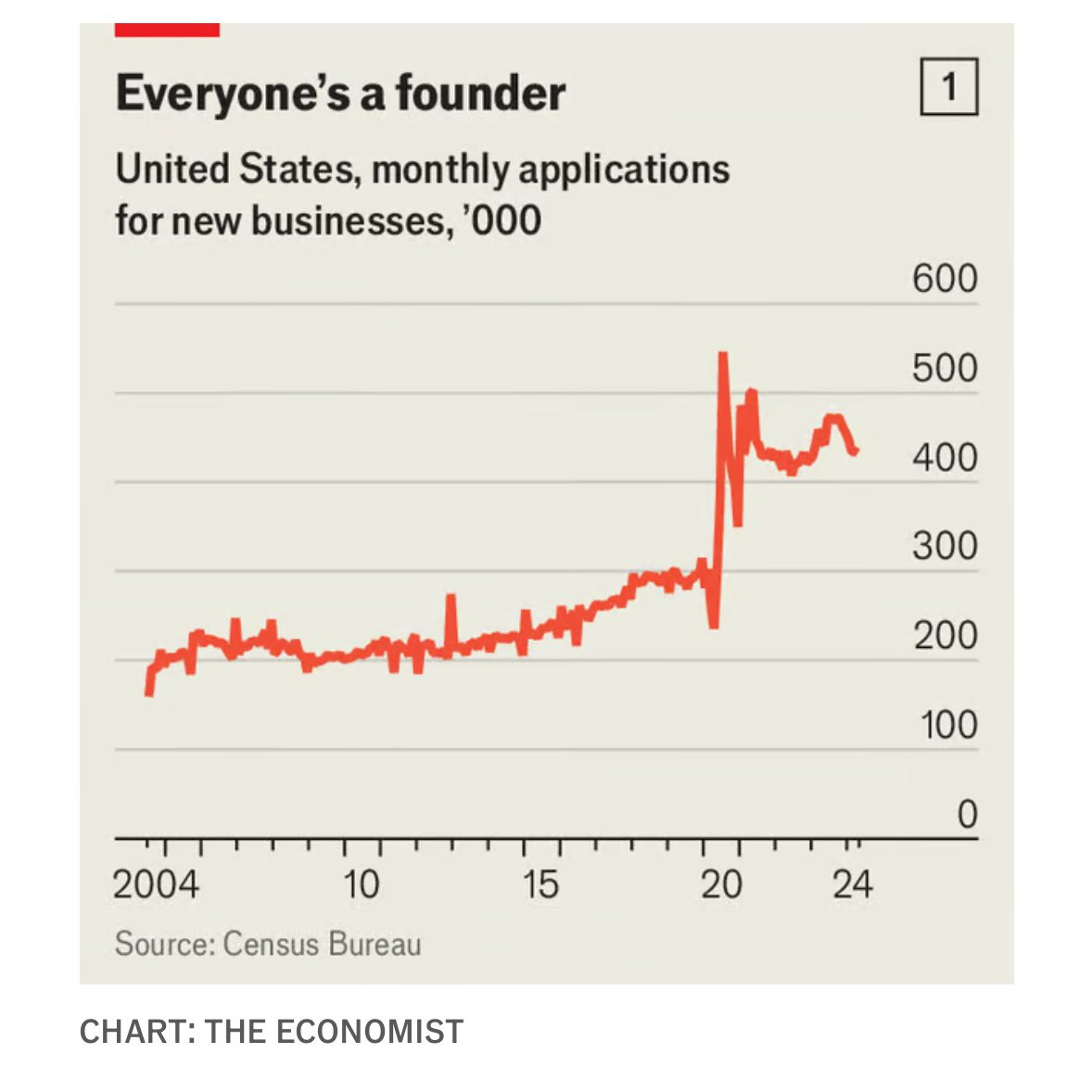
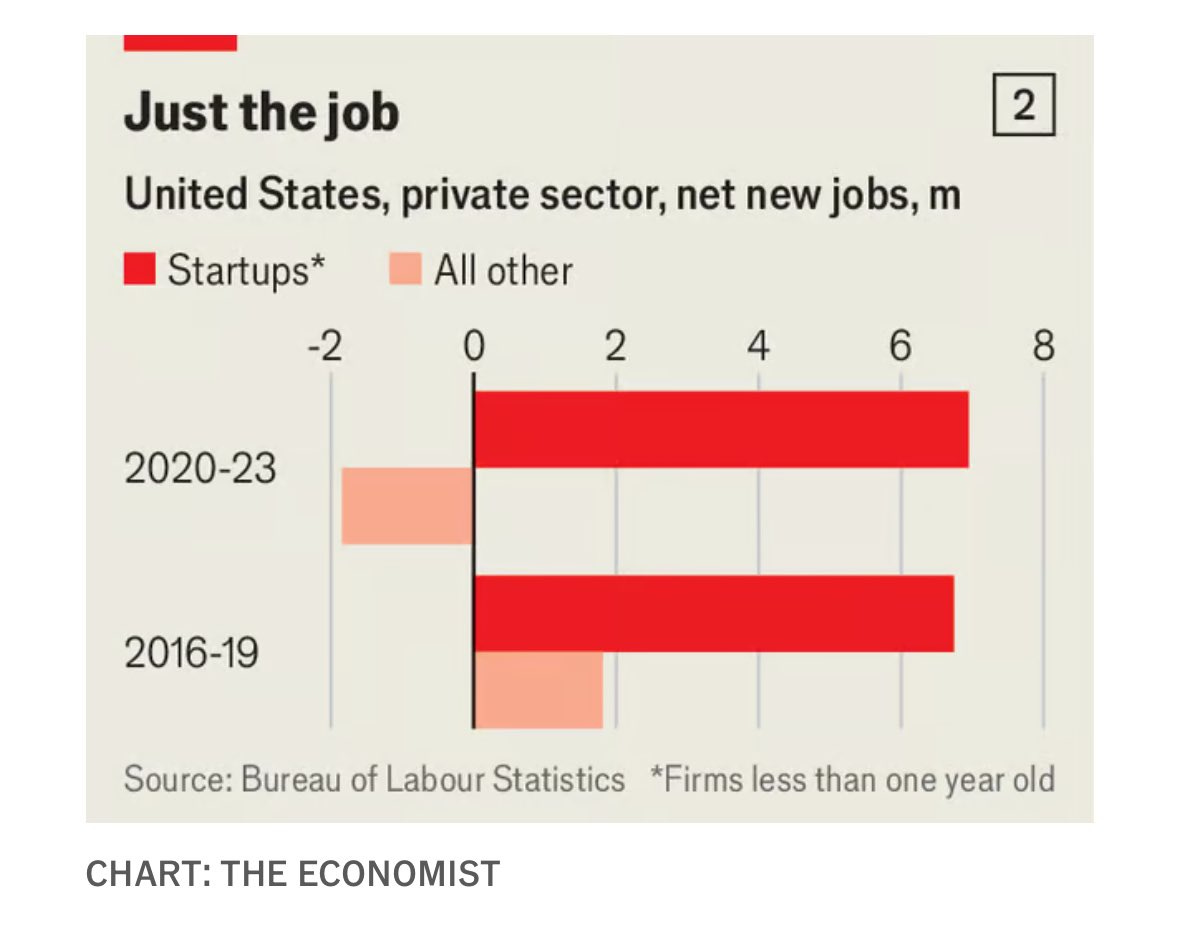
Startups (overally, not specifically in tech or backed by VC), meaning firms less than one year old, are now producing more than all of the net new jobs, and there are a lot more of them than pre-pandemic.
Alec Stapp: Incredible statistics on US startup boom:
“In the four years before the pandemic, established firms added one net job for every four created by startups.
In the four years since the pandemic, established firms have actually lost one job for every four created by startups.”
Seth Burn: I think this is darker than you realize. Established firms shrinking is not a good thing in general.
The reconciliation is that venture capital is not that important as a share of new firms. Venture capitalists talk as if they are the source of all new firms, yet they fund companies responsible for only (Claude’s estimate) 5%-10% of new jobs at firms less than a year old.
The venture capital response is those firms are the ones that grow to be giants, that change the world. And that is indeed disproportionally true. Yet one should not neglect the possibility of creating other types of firms. With AI in play, you can more easily raise venture capital for AI projects, but also consider whether it means you are in less need of such funding as well.
No matter how tough, yes Esther Crawford made it work, but as Paul Graham reminds us do not put all your savings into your startup and yolo when you cannot raise money. Decide what you are prepared to put at risk early on, and stop there. If it dies then it dies. Take the inability to raise money or make money as strong evidence. Otherwise, you are taking on the worst kind of adverse selection, and forgetting that you are the easiest one to fool, and that being a founder involves intentionally fooling yourself quite a bit.
VCs will often promise to fund you in the future if you do X. Do not believe them. They are lying. Period. VCs use this to string you along and get a free option. I mean, there’s not actual 0% they will fund you if you meet the condition. Chances are higher than if you don’t do X. But the chance is still low.
Also, startups are just flat out really hard and require solving lots of hard problems, and you never hear about most of them, my experience confirms this.
Paul Graham: Even in the most successful startups, even many years in, the founders are dealing with hair-raising problems. They mostly conceal these struggles from the outside world and even from their own employees. There’s no upside in talking about them. But I hear about them.
Because startups are so much harder than they look, a lot of people think that successful startup founders just got lucky and had piles of money dropped in their laps. But this is so not true. Between t=0 and piles of money, they deal with novel crises every couple months.
What’s uniquely hard about running a startup is that you don’t merely have to endure adversity, but have to solve intellectually difficult problems while doing so. It’s like trying to find integrals while being chased by a lion.
The weirdness is that founders also, by the Graham theory, need to be overconfident, and it would be good for more people starting out to not appreciate how hard it is going to get.
Some key red flags to avoid in your startup, including on your YC application.
Melia Russell: Applying to YC?
@daltonc and @mwseibel reveal their biggest application icks:
– too many extracurriculars tied to startups (their advice: just start building)
– hedging that they might still go to business school
– bloated founding teams
– ownership weighted toward biz cofounder [as in, highly lopsided]
Paul Graham: The point about extracurriculars is a subtle one, but it’s a red flag for me too. The best founders don’t spend college *talkingabout startups. They spend their time working on projects, whether they’re meant to be startups or not.
I’d rather fund someone who knew zero about startups and had a lot of experience building things. Startup basics are easy enough that you can learn them during YC. But you can’t learn to build things.
Evan LaPointe: Bummer. They’re just penalizing honesty around extremely fixable issues. Too easy to manipulate these answers (and too obvious to those who would).
These are real red flags. As in they are things founders should be avoiding whether or not anyone will find out about them. They do not bode well. They are partly causal.
I strongly endorse that you want to be building things first and foremost, that you should avoid a bloated founding team or a lopsided equity distribution, and that you should not be in the ‘maybe business school’ mindset.
I do also notice this advice favors YC and VC. Learning the startup side later is underrated, but also is what a venture capitalist would want you to do, for their own business. VCs are always telling you not to worry about such things, except when they are explaining the importance of a particular detail. Which often happen exactly when it is too late to fix the problem this go around.
This post is full of advice given freely at least twice over. Why is that?
Paul Graham: The techniques for getting rich from startups are very valuable, but the people who know most about them make no effort to keep them secret. Founders and investors publish them openly.
The investors are motivated partly by self-interest. They want more people to get rich so they can invest in them. But mostly (and almost entirely in the case of founders) those who publish the techniques for getting rich just want to help people. This is not a zero-sum world.
Since people who get rich from startups demonstrably get richer than those who get rich in other ways, there should be zero market for people selling “secrets of getting rich.” Why would you pay for something inferior to the free alternative?
Now that I think about it, I bet I know how the people who sell “secrets of getting rich” manage to do it. Presumably they’re claiming to sell secrets of getting rich without doing much work. Yeah, good luck with that.
I do think a lot of people offering advice purely want to give back and help people, and make the world a better place with more wealth and nice things and cool toys. That is totally a thing.
I would be precise with the self-interest argument.
The VC does not want you to get rich so they can invest in you. They want to invest in you now, on favorable terms, and for you to then make them and ideally also yourself rich after.
If you are literally (or at least approximately) Paul Graham, sure, you can plausibly rise the tide enough and benefit enough from the rising tide can lifting your boat that this makes sense. That is a very small club.
What is largely going on instead is that the VCs are trying to compete for deal flow, and they are trying to shape investor attitudes in ways that benefit themselves and other VCs. If you are known for giving great advice, founders will think of and think well of you, and you will get more opportunities. Getting the best opportunities is key, perhaps the most important key, to success in VC.
The other half is promoting techniques that make founders do what VCs want in general, which raises your status and valuable connections with other VCs. You want the founder to build a useful product and a great company that you can get a lot of for not that much. You do not want the founder to care about positioning themselves to get a good deal from VCs or taking advantage of the flaws in the system.
If you give advice that makes founders give VCs good opportunities, you are well-poised to capture exactly the customers you generate. And other VCs will notice you helping VC interests and cooperate with you.
There is still lots of very good advice on how to found and run startups. Mostly what the VCs want you to do is a good idea for you as well. You can do well mostly following the standard advice playbook, and you will probably do quite poorly if you are unaware of the contents of that playbook. To do the best, you need to recognize how the playbook was crafted, and where it is a trap.
If you are tall, you can hope to be allowed to run someone else’s company. If you are short, perhaps start your own instead? Also, reminder: How much of discrimination against women is actually discrimination against short people?
Noor Siddiqui: In the US, 14.5% of men are 6ft or taller.
Among CEOs of Fortune 500 companies, 58% are 6ft or taller (4x increase)
3.9% of men are 6’2’’ or taller, among F500 CEOs, 30% are 6’2’’ or taller (7.6x increase)
From Blink, by Malcolm Gladwell
Dave Lu: Self-made American billionaires who didn’t have to get picked for the CEO job and built their own Fortune 500 companies:
Mark Zuckerberg: 5’ 7”
Jensen Huang: 5’ 7”
Jeff Bezos: 5’ 7”
Michael Bloomberg: 5’ 7”
Eric Yuan: 5’ 7”
Tony Xu: 5’ 7”
Sergey Brin: 5’ 8”
Bill Gates: 5’ 10”
But also, notice that women have their own cheat code, and unlike height it is something they can change if they want to…
Noor Siddiqui: In the US, 5% of women are blonde. Among female CEOs of Fortune 500 companies, 48% are blonde.
Female senators: 35% blonde.
Blonde privilege but not height privilege for women apparently. Just 2.2% of male F500 CEOs are blonde.
Correlation is not causation, the decision to change one’s hair color is indicative of various other things as might be having that hair color naturally. But yes, if you are looking to be a female CEO or politician or do anything similar, you want to choose to have blonde hair.
I found this illustrative in multiple ways.
Paul Graham: Doordash has to win because Tony Xu is the optimal founder of such a business. If you were designing someone for the job, you wouldn’t change a thing. So if there is a business there at all, which there clearly is, Doordash will inevitably dominate it.
Serpunk: What makes Tony the perfect founder for this business paul?
Paul Graham: He loves the parts of it that would bore or frighten or confuse a normal person.
That certainly is an asset. But what I found most illustrative here is the extreme faith by many venture capitalists that the right founder will win, no matter what else is happening, even this late in the game. I do think it’s easy to underestimate such impacts, but there are a lot of things going on and indeed do many things come to pass.
DoorDash seems ahead, and I think Caviar, which they own, is the best option in NYC by a lot if you’re not going low end on your order. But I don’t think anyone ever ‘has to’ anything, and in many ways the original DoorDash actually has substantial issues that I would have thought a detail oriented founder would deal with.
It’s not the incentives, it’s you, but also it’s the incentives.
Gokul Rajaram: Friend in venture: “I think half of the mania in venture growth is explained by young deal makers who want to just jam shit in the portfolio and make a name for themselves.
There’s a nice good business that’s single digit ARR, 3x’ing this year, and ahead of plan. But principals and junior partners at many firms are chomping at the bit to deploy capital and so are treating it like God’s gift to humanity.”
Like @garrytan said, this is a prime example of a principal-agent problem.
The way most firms (VC/PE) evaluate junior team members is deals done vs. outcome. Promotions happen long before the expected exit becomes apparent. So junior investors are incentivised to do deals that the firm will sign off on vs. be patient for the right deal.
The challenge with “right deal” is junior investors don’t have the ability to pick their deals, so even if you find the Coinbase/Doordash Series B and advocate the hell out of it, the IC may pass.
So ultimately the incentive structure (at most firms) makes you advocate for deals you believe the IC will do. If it does well then you can claim it as your own. If it doesn’t then you a) either got promoted and found some deal that worked b) work somewhere else and sweep it under the rug c) leave for the operating side.
Garry Tan: Principal agent problem meets OPM.
Founders, if you wonder why VC’s act so weird, it’s basically this.
VCs act mostly via mimesis based on social consensus, but the future is built by founders who are contrarian AND right.
The unfair result is that “hot” spaces get a lot of money and “cold” spaces get no money, and the reality is great companies are somewhat arbitrarily either showered with outside capital or never get any.
It’s one of the strangest examples of pervasive capital misallocation.
Tyler Hoggle: 🐑 vc.
Garry Tan (CEO of YC): Nailed it.
Yes. Unfortunately, this means most VCs cannot get you a lead or first investor to recruit the rest.
It took very little direct experience advising a venture capital firm to see these dynamics in action, even if everyone involved was doing their best to avoid them. It is very hard to deploy the strategy ‘do what maximizes returns’ or to go outside of the social consensus. There are huge gains for venture capital willing to play to win.
Remember that even Paul Graham, who I am sure is doing great anyway, has said that he knows he could get even better returns by changing his investment heuristics away from consensus, yet in practice he can’t execute on that.
Given that, why would one claim that VCs must be acting efficiently? There is so much to unpack here:
Paul Graham: People casually claiming that VCs discriminate against this or that group should also mention that VCs have the strongest incentive not to discriminate of any group in the world. They personally lose money if they pick the wrong founders.
Because of this, they’re very quick to change their behavior if they realize they’ve been discriminating against some kind of startup. In fact, they are famously, comically quick to.
VCs are constantly, and rightly, ridiculed for jumping on one bandwagon after another. But think about what that means: they previously refused to invest in such startups, and now are eager to. I.e. they realized they were discriminating against them, and now are overcorrecting.
How do they realize they discriminated against startups of type x? When startups of type x start to do much better than they expected. That may seem a strange definition of discrimination. But actually it’s the only definition that makes sense.
If multiple companies founded by Martians with eyes on stalks started growing really fast, VCs would be falling over one another to invest in more companies founded by Martians with eyes on stalks. You know they would.
It would be nice if people responded to incentives this way. The discrimination literature makes clear that they do not, and also some amount of discrimination (in this sense) makes sense for founders socially and also financially, because those around them are doing the same, and also they are messing up.
If one takes this story at face value, it is saying that VCs update too strongly on recent outcomes, and pattern match to prior successful companies without understanding what matters. They are in the overcorrection business, in the ‘what’s hot’ business and the pattern matching business.
If you are in the overcorrection business, you are discriminating against most groups most of the time. You are looking for a set of patterns, and woe to anyone lacking those patterns. Which is indeed how I believe VCs operate. And also that is what discrimination means here.
Why do they do this?
Because VCs are largely concerned with how they look to other VCs and socially justifying their decisions.
And also VCs who invest are and should be very concerned about who will invest in subsequent rounds, and how easy it will be to raise.
Eliezer Yudkowsky (responding to top of thread): I put that claim to Peter Thiel once, and he replied to me that VCs need to be very concerned about every kind of fashion; because a startup investment won’t thrive unless other VCs want to fund its later stages downstream.
Paul Graham: Are you sure? It’s unlikely that he would say that, because the later the stage of investment, the more all that matters is revenue growth, and surely Peter is experienced enough to know that.
Eliezer Yudkowsky: I am reasonably sure that it is what Peter Thiel said to me; it stuck in my mind at the time.
Paul’s statement here is not credible. Of course things other than revenue growth matter. You would be crazy to ignore all other factors. Even if all other VCs only care about revenue growth, in which case you would mostly also have to only care about it, you would still be wise to look at other things.
Things people say when not currently talking price.
Paul Graham: There is no such thing as value investing in venture capital. The steep power law distribution of returns means you want to be in the best startups at whatever the price happens to be.
What’s the difference between a high valuation and a low one for a comparable company? 5x? If you use that as a selection criterion in a domain where the difference between a big success and a small one is 100x, you’re innumerate.
Price always matters. Every good gambler knows. Every trader knows. A VC is both. That which is a good deal at $1X is often a bad deal at $2X.
True, it will probably either pay out $100X or $0, but so what? You don’t know which is which yet, you only know your guess on the odds. The key is getting a good price, which gives you good odds. What counts as a good price is different with startups, since they are all growing rapidly. The best ones really are worth a lot more relative to their baseline numbers, and you should pay that extra amount.
What Paul is actually saying here, as I understand it, is that the most valuable startups are indeed underpriced. That they are the value.
And I think this is actually true. Relatively unpromising startups find winner’s curse investors who give them a reasonable price, and they hold out for that solid price because if you take a bad price your chances of success drop enough you might as well go home.
Whereas if you have an amazing startup, what do you do? You go after the best investors that can offer strategic help and will reliably follow in future rounds, and you do not need to worry so much about the exact price, whereas you do have to worry about a potential down round or other strangeness if you leverage your position now and then things go badly. And all those top VCs are of course telling you to price ‘only’ 5x what the unpromising companies charge, when we all know you are 10x or 20x as valuable. But that’s because people are making the wrong comparisons.
What is an underrated good sign to look for as a VC? How about fun.
Paul Graham: YC is different from most other businesses in that you don’t have to trade off fun vs money. The founders who are fun to work with also as a rule tend to be the ones who are most successful.
As with many similar Paul Graham observations, it is wise, and the consideration underrated, yet it is overstated. The question is why Graham and also other VCs are unable to properly update based on such factors.
Another Graham observation is that you want to let startups be themselves rather than telling them to copy others. To what extent does practice follow this principle?
Paul Graham: Someone at a dinner party last night was curious why YC doesn’t provide office space to startups. I explained that it was because successful startups have a very strong flavor of themselves, and you don’t want to do anything to dilute that.
…
It’s good for each startup to be in the same place much of the time, but they don’t have to be in the same place as other startups more than a few hours a week.
The key is ‘when faced with a choice’:
Greg Brockman (cofounder OpenAI): In startups, when faced with the choice between an easy and a hard path, the hard one tends to be where the value gets created.
Easy is better than hard. You knew that. It is when the choice is tricky that the hard path likely creates value.
Especially beware when things are hard that should be easy. In particular, when raising funds or getting customers is hard, that is not a sign that pushing harder will create value. It might, but the sign is that you likely are going down a wrong path.
Thus: Paul Graham gives the good advice to only raise funds if it is going to succeed. Of course, that means you have to figure out if you will succeed.
Paul Graham: It’s a mistake to try to raise money if you’re not quite attractive enough to investors. They don’t say no immediately. They suck up a lot of your time and hope, and then say no. It’s a huge distraction and crushingly bad for morale.
The most important factor is your growth rate, if you’ve been launched for long enough to estimate it reliably. If your growth rate is 4x a year you’re definitely attractive. If it’s only 1.5x a year, you’re not, unless it’s a late stage round.
One key is that when you get a yes, it’s usually much faster than a no. Raising funds is likely either easy or impossible. If you fail to get a quick yes when you ask, you can interpret this as likely nos. The nos not being quick is better news than them being quick, but does more damage.
Thus, with the latest company I considered founding, we asked a few people, noticed fundraising wasn’t easy, and decided fine we will go do something else.
The obsession with growth rate that Graham observes is dumb, and of course there are many other elements in play. VCs are not that simple minded.
What is missing here is the impetus to think backwards. If you can only raise under some conditions, are you backchaining to ensure you get those conditions?
Paul Graham would say no, that’s doing it wrong, you should build something people want, do the right things, and let the VCs take care of themselves. That is what a VC wants you to do, but any gamer knows how dumb it is not to check your victory conditions or what gets you past the checkpoints.
When pitching your seed stage startup, Y Combinator’s Michael Siebel and Paul Graham say avoid the flash and concisely get to the point, among other things in an hourlong presentation. Again, keep it easy.
Another thing he says up front is that founders hold a special place of hatred for investors who reject them. That was not my experience.
I hold a special place for those investors who strung us along. Who made us think they would invest, then didn’t. Or, especially, for those who did that, then announced they were altering the deal, and told us to prey that they would not alter it any further. They can go ahead and rot in hell.
If you heard the pitch, and you said no, not interested? I had zero problem with that. On the few cases they also explained why, they have my sincere thanks.
On a similar note: Patrick McKenzie notes that if you write an investment in a startup down to zero, it is your moral obligation to ensure the founder knows this, and it would be good if you outright returned the investment so you were no longer in any sense their boss (or, I would add, crippling their cap table). Most importantly you want to let the founders know not to waste everyone’s time any further, and let them know they have failed with honor. When someone finally did essentially tell me this at MetaMed, it was refreshing and helpful, even if their ‘we will back your next play because we still believe in you’ did not go so well.
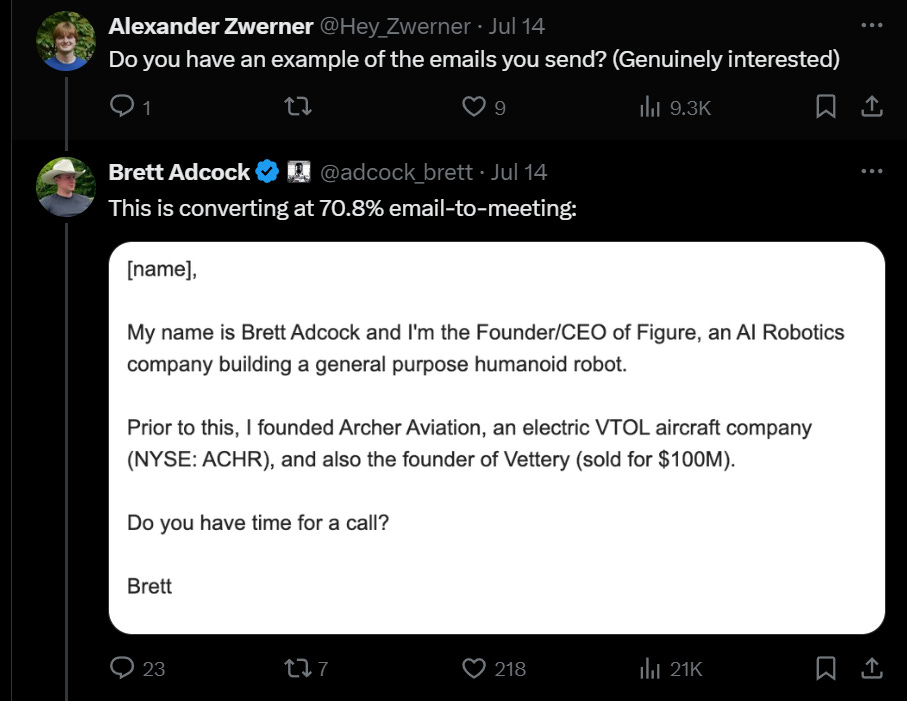
Brett Adcock, who says he has raised $1.7 billion, says most of it was via cold emails. He says cold is better because this is a shots-on-goal game, and cold emails scale, whereas networks do not scale so well and it is hard to get people to actually advocate for you.
Except, this number might be a hint something is odd.
To state the obvious, no one converts to a phone call at 70%. That’s why he calls it a ‘shots-on-goal’ situation. To the extent that email is working reasonably often it is because people know who he is or what his prior companies are. This is the opposite of a traditional cold email scenario, where no one has any reputational reason to listen to you. I mean, sure, if Taylor Swift ‘cold emailed’ me I would take the meeting.
Your periodic reminder, here from Patrick McKenzie, that talking to an associate at a VC firm is probably a waste of your time. They have no authority. This time spent is not going to lead to a deal very often.
Darren Marble: Talking with a VC Associate will almost never convert into actual funding.
Just stating the facts.
Yuri Sagalov: A lot of GPs at big funds that have associates are quote-tweeting this saying this is not true.
Notably missing are founders quote tweeting this saying that it is not true.
Empirically, it *istrue.
Darren said almost never, not never. And almost never is correct.
Greg Brockman: Common mistake in a startup is to serialize subprojects that could be parallelized.
I worry about selection effects here as well. A large portion of startups I have seen attempt to do too many different things at once, and would have been wise instead to focus. If there are multiple steps that are part of the right focus, then by all means work in parallel. But this in sharp contrasts to staying lean, shipping quicky and so on.
What good are hackathons? I agree with Patrick McKenzie here, that the point is to prove to everyone especially yourself and have a culture of You Can Just Make Things. And also to have a chance to brainstorm some of those things and see which are worth just making, and networking, but that is secondary. Understand how much trivial inconveniences and paperwork barriers, let alone bigger problems, stop progress.
Don’t play house. Rather than go through expected motions, instead do things for reasons, try specific things and so on. Only go through expected motions when you are being evaluated and rewarded by those checking for the motions and you mostly care about those evaluations and rewards (such as is often true in school), start-ups are different. That much is wise.
I do think Paul Graham takes it too far, trying to convince founders to be fully genuine and build things people want without caring about investors, because that is what is best for the investors.
You do need to do the actual building. Focusing only on fundraising won’t work. But also acting like you don’t also need to invoke Goodhart’s Law or target what gets you funded won’t work either.
We are teaching our most talented children not to follow their curiosity.
Paul Graham: I gave a talk about startups to 14 and 15 year olds, and their questions afterward were better than I get at top universities. I puzzled over this, then realized why. Their questions were motivated by genuine curiosity, rather than to make some kind of comment or to seem smart.
The best one was one I hadn’t even considered when I was writing the talk. I listed three things you needed to start a startup — to be good at some technology, an idea, and cofounders — and one kid asked what other things besides startups this recipe worked for.
Patrick McKenzie: We are very good about teaching people to play bad games, and not very good about teaching them introspection on whether the game is a good or bad one, in part because you have to win the bad games repeatedly for years to end up teaching them.
Paul Graham: The more I learned about how badly US college admissions are done, the more puzzled I was that there was any correlation between where startup founders went to college and how their companies did. Then I got it: mismanaged college admissions are ideal for selecting founders.
US admissions departments make applicants jump through arbitrary hoops that have nothing to do with intellectual ability. How could this test matter? Answer: the more arbitrary a test is, the more it’s simply a test of determination and resourcefulness.
Determination and resourcefulness are the best predictors of startup success. So the worse a job admissions departments do of selecting potential students — the more arbitrary their criteria — the better a job they do of selecting startup founders.
If you are measuring determination and resourcefulness, that doesn’t seem like such a bad admissions policy? Except of course that it means it eats your entire childhood. But that is not the school’s problem.
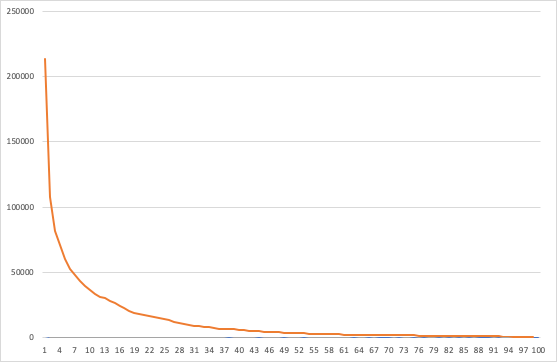
Replit has a course called 100 days of code. A lot of people do day 1.
Paul Graham: How many people make it through each day of Replit’s online 100 Days of Code tutorial.
This is ‘Emergents TCG user retention’ levels of not retaining users. How should we think about it?
Andrew Davidson: After day 10 or so I just wanted to start experimenting on real stuff… which coincidentally Replit makes really easy with its Al generate and explain features.
You can just ask Replit to create you some bespoke lessons on the fly. More fun!
Amjad Masad (CEO Replit): Most people don’t need to go past day 14 to start making things & learning on the job.
Samuel Path: In the course description it says 15 minutes per day. But then later it turns out that many days require more than 30 minutes. For busy individuals, finding 35 minutes a day is not the same challenge as finding 15 minutes. Maybe they should be more precise in the intro.
Michael McGill: You become part of the 99th percentile just be consistently showing up.
There are not literally zero stupid questions, but in math, basically, yeah.
Daniel Litt: In my experience “asking stupid questions” in mathematics is often correlated with “wanting deep understanding.” (And, in my experience, being annoyed at “stupid questions” is often correlated with “wanting to look smart.”)
QC: Agreed. I can’t remember the last time i was annoyed at someone for asking a “stupid question” in math. literally all of the questions I’ve ever been asked directly 1-on-1 are great and i love answering them, and i deeply appreciate people’s hunger for deep understanding
The closest i get to “being annoyed at stupid questions” is sometimes I’ll come across questions on, like, quora that either 1) are just word salad, or 2) that reveal really large gaps in understanding that sometimes feel like they’d be incredibly exhausting to try to explain.
It is essentially impossible to ask a stupid question in math if you indeed are curious and do not know the answer. In other areas it is easier, but it is still hard.
Especially if you also note you are asking a kind of a stupid question, and even better if you have even checked with an LLM? Very hard.
Paul Graham: Someone asked me if they need to learn to program to start a startup, and I realized my answer depends mostly on two things: how old they are, and whether they already have a cofounder who can.
If you’re 20 I’m always going to say you should learn. 20 is too young to start claiming you’re “not technical.” It’s too young to claim you’re not anything. Whereas if you’re 40 and already have a cofounder who can program, ok, you can skip learning to yourself.
My experience is that it is a serious handicap if you cannot code well enough to contribute. Do your best to fix that. Even if you do not directly contribute, if you do not know how to code at all you will not understand what is going on or make good decisions. You need to learn enough to be able to discuss problems and solutions, at least on the architect level, no matter what.
AI is going to change the equation. There is increasingly little excuse for not knowing how to code. You could instead say you will no longer need to know how to code. I disagree. My experience is that AI coding goes dramatically better if you understand what is going on.
New Paul Graham essay on the value of Superlinear Returns. His case is that in many places wins compound and there are increasing marginal returns, so you want to go all out and be more ambitious and focus on growth and work on your own projects and follow your curiosity and take risks and do all the Paul Graham things and YC things.
Seemed like a lesser work to me, an attempt to deliver the message (that I mostly agree with) in a new way that didn’t really work. But then, the whole point is to take risks that aren’t actually risks.
Reid Hoffman echoes the standard rule that the best founders don’t have work-life balance. Startups are all about concentrated effort and super-linear returns and going all out. That does not mean that it is not worth creating a startup if you cannot work 80 hour weeks. Non-best founding efforts are still worthwhile. But yeah, if you get traction, look into not having any balance for a while.
A fun story about the kinds of things startups do when they have to, such as showing up at the back-office document processing arm of your lender when they demand you file physical copies of forms and won’t process your loan without them and there’s a backlog.
Yes, it’s illegal discrimination, but is it wise?
Kevin Fisher: I was in a discussion with a young founder who said “no kids” was their metric for hiring because “they’re not committed” 🙈
@ Young Founders – Hours are a bad proxy for commitment. People can work long hours for all sorts of reasons.
What you’re looking for is emotional and spiritual alignment with what you’re bringing forth into the world. You want people who are putting their life energy into your vision for the future.
Going to sleep, waking up, and thinking about how to move your mission forward. Dreaming in your vision. Hours are a byproduct of alignment not the goal.
I had one job that very explicitly said to me during the hiring process that they prefer to hire people without families. And indeed I can see why. I worked very long hours, lived and breathed the work for years, and this was highly profitable for all concerned. If I’d had other demands on my time, I would have been less effective. Yes, life requires that we all indeed do have other demands on my time, and I did indeed pick those up later. Also having a family and especially children is a great inspiration and motivator. But whatever the law might say, we should not kid ourselves that some jobs greatly benefit from a lack of commitments.
At one point, after many years of competitions, it was observed that no (at the time) parent had ever made the top 8 of a Magic Pro Tour. I do not know if that is still true.
The good news is that most other jobs are not like all this. He said, working a lot more than forty hours.
Revenue, or at least profit, wins in the end. Eventually.
Paul Graham: Startups get compared by how much they raise and at what valuation, because that’s public information. But this has the unfortunate side effect of making fundraising read as success. So I’m glad YC publishes a list of the top companies by revenue.
I would have been impressed if that list was for the 2024 YC class. Instead, it is a list that draws from all of YC’s history, so it includes firms like AirBnB. At that point, I am not sure it makes that much difference.
Why are you told to focus so much on revenue?
There are three distinct reasons. It is important to understand all three and know which ones matter to your business.
-
Revenue gives you money. That money means you have to raise less funds, perhaps even zero funds, and do it less soon.
-
Revenue is a proxy metric. If you seek revenue you will be forced to learn how to sell, you will encounter real customers, you will build something people want.
-
Revenue determines investability and valuation. You can raise more, easier and at higher valuations, often dramatically more than the actual revenues involved.
Beware also that these can backfire.
-
You can try to bootstrap or focus on small revenues. This can distract you from understanding your actual business model, and dramatically slow you down.
-
All the usual Goodhart’s Law problems apply. Often this is not a good proxy, or it is but you can easily lean on it too hard.
-
Having revenue can shift VCs into ‘revenue mode’ where they start doing different calculations, and dismiss you as a failure or as worth less than if you had kept that angle mysterious for longer. Or you might get revenue too early that makes it hard to ‘show growth.’
My startup MetaMed experienced forms of all three of these failure modes.
Garry Tan moves YC from Mountain View to San Francisco proper, says its startups must follow.
Lee Edwards: Imagine sitting down with a mid-sized city mayor and being like – In our city, this guy made one rules change at his co to bring hundreds of tech startups to the city.
“That’s great, so they probably gave that guy the keys to the city, huh?”
No. Uh. Actually…they hate him.
To be fair to San Francisco, he is actively trying to overthrow the city government and would have tech people running the place, calling the current regime the height of incompetence and self-sabotage that has ruined a city capable of greatness.
To be fair to Garry Tan, he is actively trying to overthrow the city government and would have tech people running the place because the current regime is the height of incompetence and self-sabotage that has ruined a city capable of greatness.
San Francisco does seem like the right choice over Mountain View. The city is where the AI action is, so that is where YC should be as well. If you base in Mountain View, you are not close to the action, and you are still paying infinity dollars to be there. Yeah, the city proper is quite the dump at the moment, but if you care about that so much then YC is presumably not for you anyway.
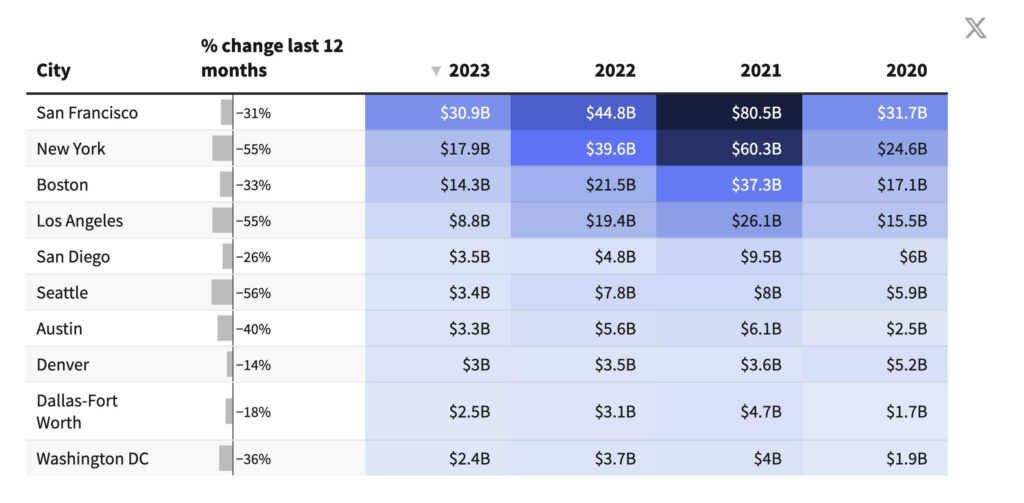
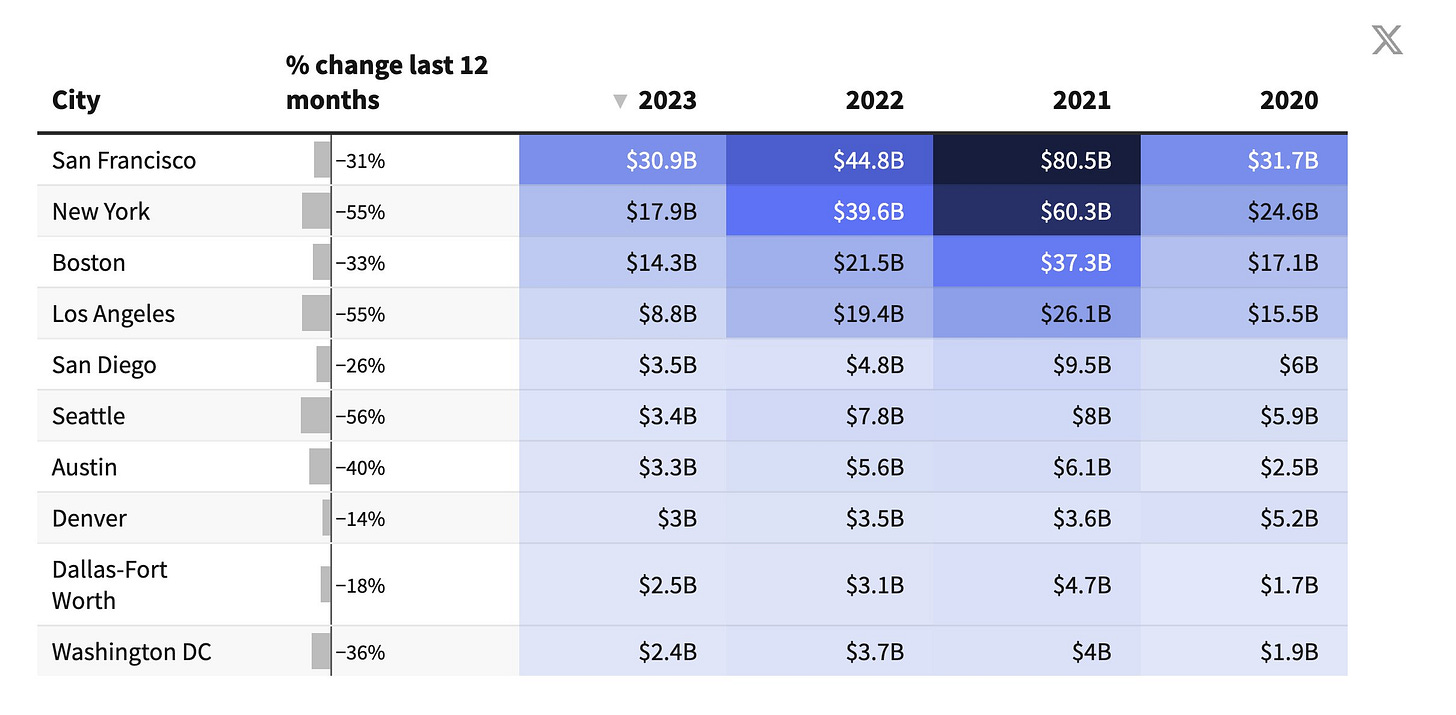
Startups are constantly told they absolutely must be in San Francisco. That this is the only place to raise money, if you are not here you are not serious, and so on. And yes it is number one by volume, but not by so much? A factor of less than two, New York is often remarkably close although it had a bad 2023 for whatever reason:
There is no doubt greater imbalance specifically in technology and especially in AI. Also there are far more sources of funding than one startup can attempt to tap, and planes exist.
The bigger story here is of course the big overall decline from the 2021 peak.
When you enable the fundraising, and also when you build better stuff, and when your connections make everything easier, you make the startups better.
Max Brodeur-Urbas: Today is day 80 and the end of YC.
Final results:
– MRR +4100%
– Daily automation runs +650%
– Finally feel confident saying we’re making something people love
Legitimately sad @ycombinator is over but grateful it happened. So excited for what’s next.
Going for another 80 [days of work].
Paul Graham: A lot of people unconsciously think of Y Combinator as a marketplace for fundraising, but this is what it’s really for: making the startups better. When YC is done right, fundraising is just a victory lap at the end.
YC changes your circumstances in ways that allow you to build something people love, and where you get rewarded based on your ability to demonstrate progress in terms of what you build and who is using it, while having a rocket that helps you find those early users, exactly because it takes care of the things that would otherwise distract you from building and shipping.
Hardware is a hard business, also a chance to do something great.
Always also ask, would it be something good? Most of the time the answer will be yes, but in the age of AI there are important exceptions. If you are making hardware that enables frontier AI, perhaps that is not a good idea.
An overview of YC’s advice to hardware startups, and a YouTube video on their hardware startups this round with Garry Tan.
Presumably an overstatement, still:
David Lieb: I’ve made or seen hundreds of hires, and one thing I have never seen is a B player hire an A player. Not once.
If you play that out, you realize that compromising on even a single role can destroy a team forever.
I have seen it happen. I do agree it is rare. The thing is, if you are an A-player and looking to hire, that’s an easy problem, you take care to hire A-players. What about if you are an A-player looking for work? How hard should you work to ensure only an A-player gets to hire you? How much should that be your priority?
I do not buy that A-players are always in such high demand that they always have A-players chasing them. If you do believe that, then your definition of A-player is different from mine. Also note that there are people who are superstars in some ways, but who should absolutely not be doing the hiring.
The ancient art of the reference check. Basic advice is to drill down into conflict during the main interview to prep, force everyone to cite an ‘area of improvement’ or otherwise say something negative and then see how far they’ll take it when paraphrased to nonchalantly sound terrible, check if they had impact, and ask about top X% (for 10/5/1) and what they’d need to get in that if no.
If they say someone else is top 1%, the suggestion is to go try and steal them. Dishonorable scum. So if they are calling you for the reference, maybe don’t tell the guy that part.
If you are debating whether to fire someone, you should probably fire them?
aviel: No one has ever regretted firing someone.
Paul Graham: This is not quite true, but it’s remarkable how close to true it is, for such a blanket statement. I know people who regret layoffs they were forced to do by higher management, but I can’t call to mind an example of anyone who regrets firing someone they chose to.
Eliezer Yudkowsky: “In those rare cases where they get to see how a fired employee performs in their next job, almost nobody reports that they inferred they should not have fired that person.” Not saying false, just observing number of filter steps.
Two examples raised in reply were Steve Jobs and Sam Altman, so yes, technically some people have importantly regretted firing someone. And as Eliezer notes, if you should with full information regret the firing, that does not mean you know that information.
Still, I believe it is true that, once you actually works up the nerve to fire someone without anything forcing you to fire someone, it is usually highly overdetermined that they had to go. You will make the occasional mistake, or turn out to be wrong, but this error mostly goes in one direction.
Mike Solana offers a warning that yes, obviously the anti-tech people will go around ambushing CEOs in tech regardless of gender or anything else, so be aware of this.
Jason: Honest question: Would these conference producers ever ambush a male CEO like that?
Mike Solana: this is an important point for founders and CEOs actually: yes, the producers ABSOLUTELY would have ambushed a male CEO like this. The failure here is entirely on Linda Vaccarino’s part for accepting an invite to code. We all know who kara swisher is. Stop feeding the serpents.
It’s just no longer possible to be angry with journalists for attacking founders and executives… who regularly open themselves up to attack. This is on x, not code (which, to be clear, sucks). now cancel your subscriptions to the media companies that hate you, and learn. ffs.
Steph Mui: founders and investors obsess over cash runway, but a founder friend recently brought up the idea of ’emotional runway’ and i can’t get it out of my head.
Running out of money kills lots of companies, but i think not enough people talk about how running out of willpower kills just as many.
Running out of money or willpower is often a sign that things are not working and you should give up, but not always. One must know when to quit, and when not to. What you do not want to to do is quiet quit on a start-up where you are emotionally bankrupt, and prolong the agony. You do not owe anyone that, you should fold.
What goes around comes around, even if someone believes it doesn’t.
Amjad Masad (CEO Replit): Someone asked me if HBO’s Silicon Valley was accurate and I said “no it is much weirder”—he thought I was joking until I told him about a talented VC friend who believes in Flat Earth yet still invests in space tech because “the government has to make it look like it works.”
Ryan Peterson: I love showing him the 3d globe with all of Flexport’s shipments.
Bob Cactaur: I could probably vibe with that VC ngl.
Amjad Masad: I heavily fwith him.
What someone whose company got acquired by Google learned at Google, about Google and how it works, interesting throughout. You have unique resources that enable great work, exacting standards to meet, potential limitless resources, and quite the gauntlet of office politics and corporate barriers to run if you want to turn any of that into a worthwhile product. Patrick McKenzie confirms the story, and offers thoughts.
Patrick McKenzie: An undercurrent of this and similar pieces, which I would like to highlight: “Firm-specific human capital” is a real thing in the world. Being effective at Google is a skill you can specialize in, independent of (and on top of) the thing you *actually do.*
And a challenge of working there is “How much of my brainsweat/care/identity is entangled with playing the game that is Google and Getting Good at Googling? And how much is everything else?” Neither extreme of spectrum is optimal for most interesting values systems.
I have had the opportunity to work with many people who previously worked at Google, and enjoy the vast majority of those interactions. But I will say a thing that must be said, for the benefit of people who will otherwise learn it the hard way:
The culture that is Google embeds a memeplex which sees organizations that do not operate as Google operates, and interprets this deviance as damage. Some people who previously worked at Google are extremely steeped in this culture and less than reflective of this fact.
Patrick warns, essentially, that if you hire ex-Googlers especially at high positions, they will be very talented, but also they will then attempt to turn their new company into an echo of Google, which likely will not be what your company needs or you want.
PoliMath adds this wise observation: When people say that something is obviously fake, they need to give a straight answer to the obvious follow-up question: If this *istrue, how would that change your view of the situation?
No more of the “this is fake but if it is real then it is good” No more of that. Don’t tell us why you think it is fake.
Tell us why you think it is *wrong*. What are the fake people in the fake story doing that you think is wrong or gross or worthy of reprimand?
This is a great example to engage the hypothetical & demonstrate your willingness to reprimand your “side.”
It’s entirely costless because (as you have said) it’s fake. So you’re not reprimanding any real people. You’re safe. No consequences, just tell us what is wrong about it.
Startup Roundup #2 Read More »