What to know about ToolShell, the SharePoint threat under mass exploitation
Microsoft fixed the vulnerability pair—CVE-2025-49706 and CVE-2025-49704—two weeks ago as part of the company’s monthly update release. As the world learned over the weekend, the patches were incomplete, a lapse that opened organizations around the world to the new attacks.
Q: What sorts of malicious things are attackers doing with these newer ToolShell exploits?
A: According to numerous technical analyses, the attackers first infect vulnerable systems with a webshell-based backdoor that gains access to some of the most sensitive parts of a SharePoint Server. From there, the webshell extracts tokens and other credentials that allow the attackers to gain administrative privileges, even when systems are protected by multifactor authentication and single sign-on. Once inside, the attackers exfiltrate sensitive data and deploy additional backdoors that provide persistent access for future use.
For those who want more technical details, the opening volley in the attack is POST Web requests the attackers send to the ToolPane endpoint. The requests look like this:
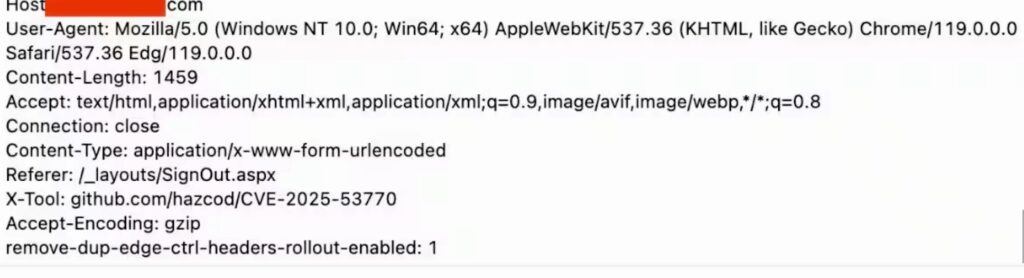
Credit: Akamai
Microsoft said these requests upload a malicious script named spinstall0.aspx, or alternatively spinstall.aspx, spinstall1.aspx, spinstall2.aspx, and so on. The script contains commands for retrieving a SharePoint server’s encrypted MachineKey configuration and returning the decrypted results to the attacker through a GET request.
Q: I maintain an on-premises SharePoint server. What should I do?
A: In short, drop whatever else you were doing and take time to carefully inspect your system. The first thing to look for is whether it has received the emergency patches Microsoft released Saturday. Install the patch immediately if it hasn’t already been done.
Patching the vulnerability is only the first step, since systems infected through the vulnerability show few or no signs of compromise. The next step is to pore through system event logs in search of indicators of compromise. These indicators can be found in numerous write-ups, including those from Microsoft and Eye Security (at the links above), the US Cybersecurity and Information Security Agency, and security firms Sentinel One, Akamai, Tenable, and Palo Alto Networks.
What to know about ToolShell, the SharePoint threat under mass exploitation Read More »

