Neofetch is over, but many screenshot system info tools stand ready
Pics or it didn’t compile —
Dev behind a popular screenshot tool checks out, but the successors are good.
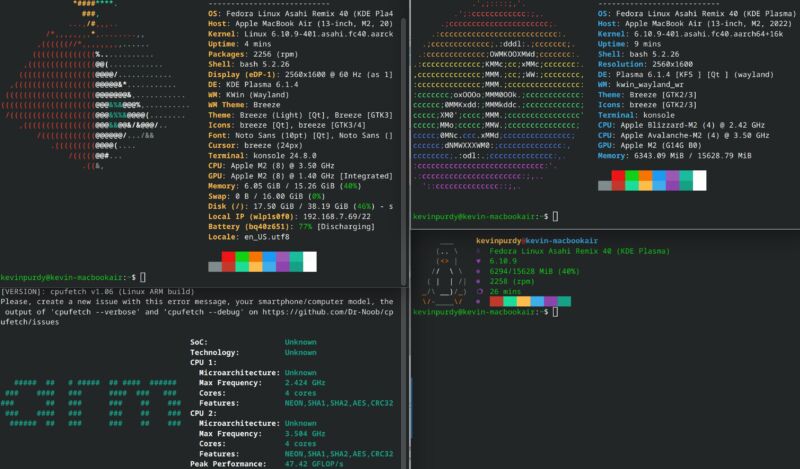
Enlarge / Sorry about all the black space in the lower-right corner. Nerdfetch does not make good use of the space it’s given—unlike the Asahi install on this MacBook.
Kevin Purdy
Almost nobody truly needed Neofetch, but the people who did use it? They really liked it.
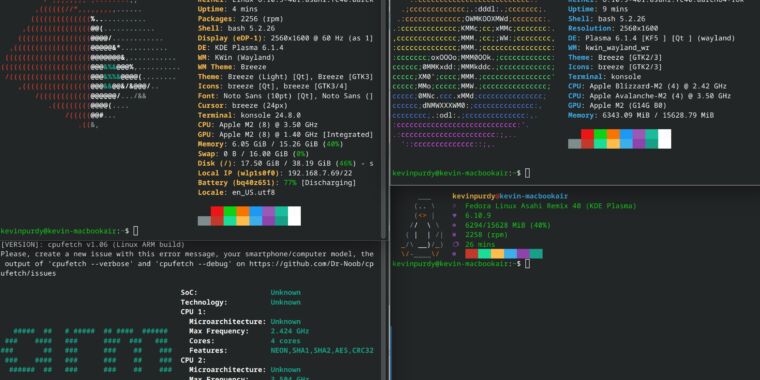
Neofetch, run from a terminal, displayed key system information alongside an ASCII-art image of the operating system or distribution running on that system. You knew most of this data, but if you’re taking a screenshot of your system, it looked cool and conveyed a lot of data in a small space. “The overall purpose of Neofetch is to be used in screen-shots of your system,” wrote Neofetch’s creator, Dylan Araps, on its Github repository. “Neofetch shows the information other people want to see.”
Neofetch did that, providing cool screenshots and proof-of-life images across nearly 150 OS versions until late April. The last update to the tool was made three years before that, and Araps’ Github profile now contains a rather succinct coda: “Have taken up farming.” Araps joins “going to a commune in Vermont” and “I now make furniture out of wood” in the pantheon of programmers who do not just leave the field, but flee into another realm entirely.
As sometimes happens, the void was filled not by one decent replacement but many.
-
Fastfetch, which is indeed pretty fast and seems to have more distros recognized (like Asahi Linux on an ARM MacBook).
Kevin Purdy
-
Hyfetch, which gives you a bunch of pride flag options on first running but can also be used without pride colors.
-
Nerdfetch, which I could never quite get to run perfectly with Nerdfonts, Cozette, or Phosphor. It’s small, which can be handy, but it mostly just shows a Tux penguin, not an OS-specific ASCII image.
-
Cpufetch, which, as the name implies, drops much more chip data into the term.
The neo-Neofetches
Fastfetch seems to have captured the default forum/thread/blog recommendation as a Neofetch replacement. It is under active development, with changes occurring just hours before this post was published. It’s highly customizable, available across most major platforms and distributions, and extensible through modules. It supports Wayland, provides more detailed memory and storage statistics, and, as the name suggests, is generally faster. It’s FOSS and has a tutorial on customizing and extending Fastfetch.
NerdFetch gives you the kind of icon customization you might expect if you’re the type who takes meticulously arranged screenshots of your desktop. By installing one of the glyph-packed Nerd Fonts, you can replace text inside your readout with icons readable at a glance. It’s available on POSIX-compliant systems (“Anything but Windows”). It lacks a lot of customization and module options, and it’s missing the big, custom OS logo (it seemingly shows a very abstract ASCII Tux in both MacOS and Asahi Linux). But it’s also compact and a bit different.
What else? There’s hyfetch, which is “neofetch with pride flags,” but it also contains inside it “neowofetch,” which is an updated neofetch sans pride coloring. The macchina system info tool is written in Rust and offers themeing, being “basic by default and extensible by design.” And cpufetch is, as you might imagine, a lot more CPU data, along with a logo. Curiously, cpufetch showed an “arm” rendering when I ran it under Asahi Linux on a MacBook, but then an Apple logo while inside MacOS. Works either way! Just interesting.
If you’ve put time into getting a Linux desktop just how you like it—or just getting Linux onto a device that really doesn’t want it—it follows that you’d want to show it off. These are not the last of the apps that will try to make fetch happen, but they’re a strong start.
Listing image by Kevin Purdy
Neofetch is over, but many screenshot system info tools stand ready Read More »