Site catering to online criminals has been seized by the FBI
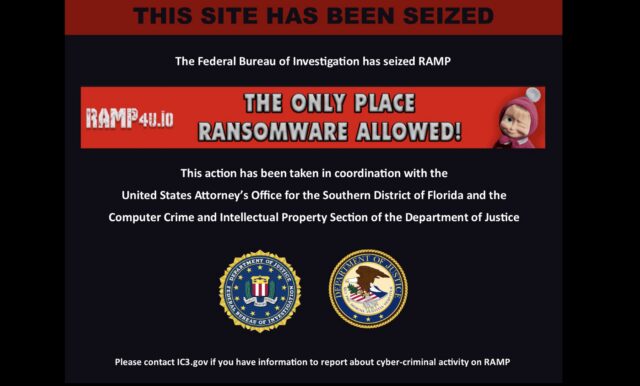
RAMP—the predominantly Russian-language online bazaar that billed itself as the “only place ransomware allowed”—had its dark web and clear web sites seized by the FBI as the agency tries to combat the growing scourge threatening critical infrastructure and organizations around the world.
Visits to both sites on Wednesday returned pages that said the FBI had taken control of the RAMP domains, which mirrored each other. RAMP has been among the dwindling number of online crime forums to operate with impunity, following the takedown of other forums such as XSS, which saw its leader arrested last year by Europol. The vacuum left RAMP as one of the leading places for people pushing ransomware and other online threats to buy, sell, or trade products and services.
I regret to inform you
“The Federal Bureau of Investigation has seized RAMP,” a banner carrying the seals of the FBI and the Justice Department said. “This action has been taken in coordination with the United States Attorney’s Office for the Southern District of Florida and the Computer Crime and Intellectual Property Section of the Department of Justice.” The banner included a graphic that appeared on the RAMP site, before it was seized, that billed itself as the “only place ransomware allowed.”
Screenshot
RAMP was founded in 2012 and rebranded in 2021, according to security firm Rapid 7. The platform served Russian, Chinese, and English speakers and counted more than 14,000 registered users, who underwent strict vetting before being accepted or paid a $500 fee for anonymous participation. The forum provided discussion groups, cyberattack tutorials, and a marketplace for malware and services. Its chief administrator said in 2024 the site earned $250,000 annually.
Site catering to online criminals has been seized by the FBI Read More »