Startup necromancy: Dead Google Apps domains can be compromised by new owners
Lots of startups use Google’s productivity suite, known as Workspace, to handle email, documents, and other back-office matters. Relatedly, lots of business-minded webapps use Google’s OAuth, i.e. “Sign in with Google.” It’s a low-friction feedback loop—up until the startup fails, the domain goes up for sale, and somebody forgot to close down all the Google stuff.
Dylan Ayrey, of Truffle Security Co., suggests in a report that this problem is more serious than anyone, especially Google, is acknowledging. Many startups make the critical mistake of not properly closing their accounts—on both Google and other web-based apps—before letting their domains expire.
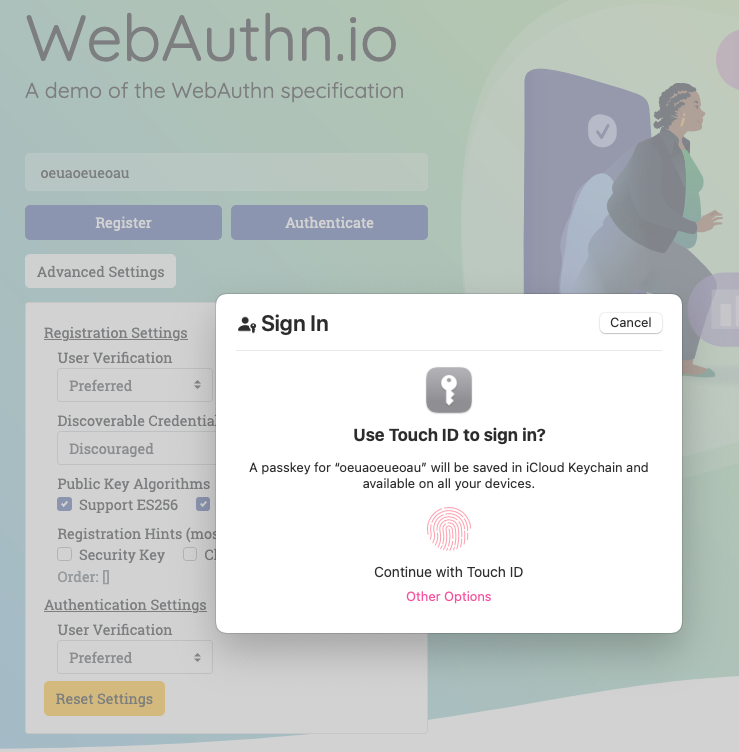
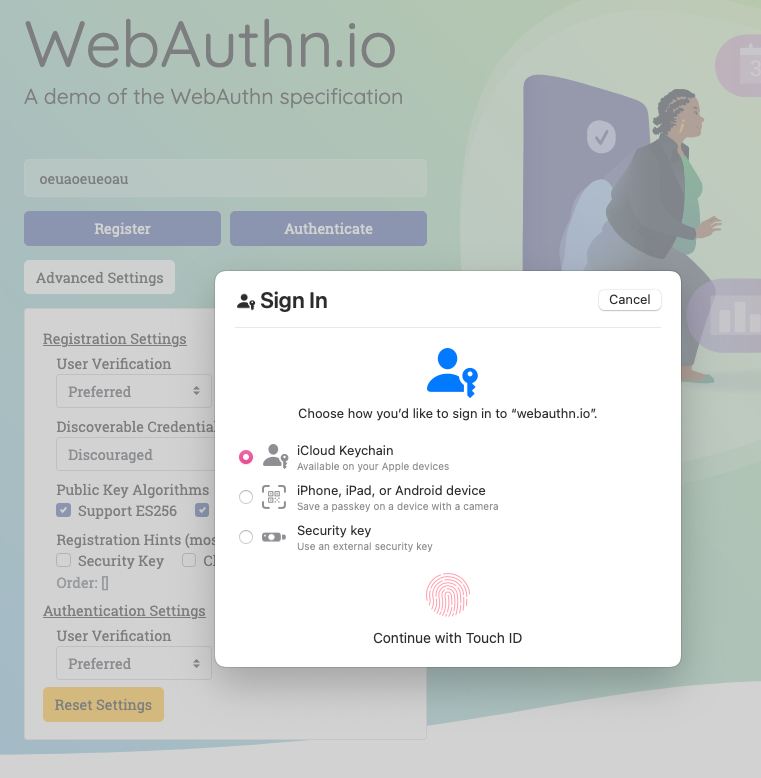
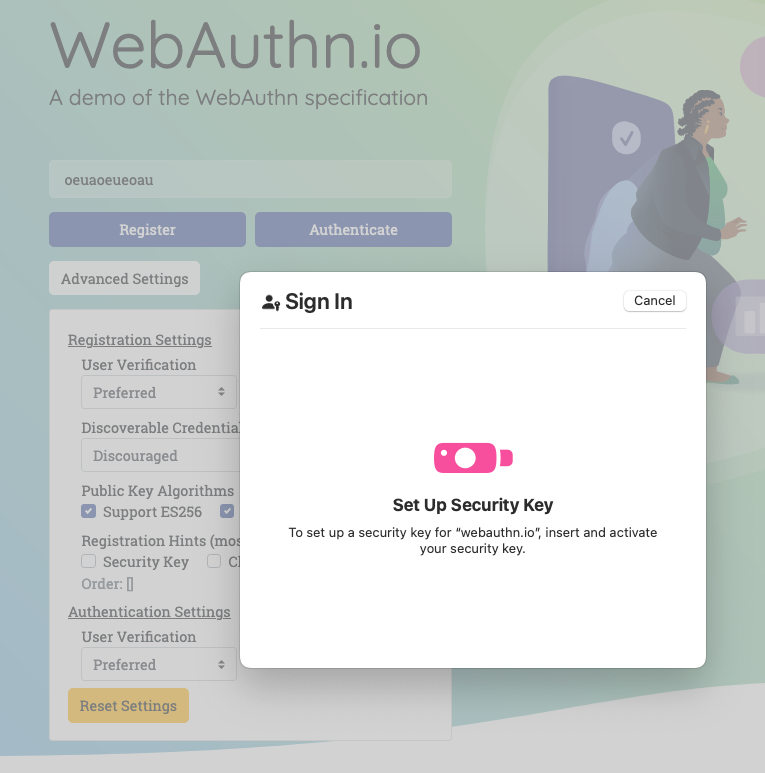
Given the number of people working for tech startups (6 million), the failure rate of said startups (90 percent), their usage of Google Workspaces (50 percent, all by Ayrey’s numbers), and the speed at which startups tend to fall apart, there are a lot of Google-auth-connected domains up for sale at any time. That would not be an inherent problem, except that, as Ayrey shows, buying a domain with a still-active Google account can let you re-activate the Google accounts for former employees.
With admin access to those accounts, you can get into many of the services they used Google’s OAuth to log into, like Slack, ChatGPT, Zoom, and HR systems. Ayrey writes that he bought a defunct startup domain and got access to each of those through Google account sign-ins. He ended up with tax documents, job interview details, and direct messages, among other sensitive materials.
You have to close up shop, not just abandon it
Reached for comment, a Google spokesperson provided a statement:
We appreciate Dylan Ayrey’s help identifying the risks stemming from customers forgetting to delete third-party SaaS services as part of turning down their operation. As a best practice, we recommend customers properly close out domains following these instructions to make this type of issue impossible. Additionally, we encourage third-party apps to follow best-practices by using the unique account identifiers (sub) to mitigate this risk.
Google’s instructions note that canceling a Google Workspace “doesn’t remove user accounts,” which remain until an organization’s Google account is deleted.
Notably, Ayrey’s methods were not able to access data stored inside each re-activated Google account, but on third-party platforms. While Ayrey’s test cases and data largely concern startups, any domain that used Google Workspace accounts to authenticate with third-party services and failed to delete their Google account to remove its domain link before selling the domain could be vulnerable.
Startup necromancy: Dead Google Apps domains can be compromised by new owners Read More »