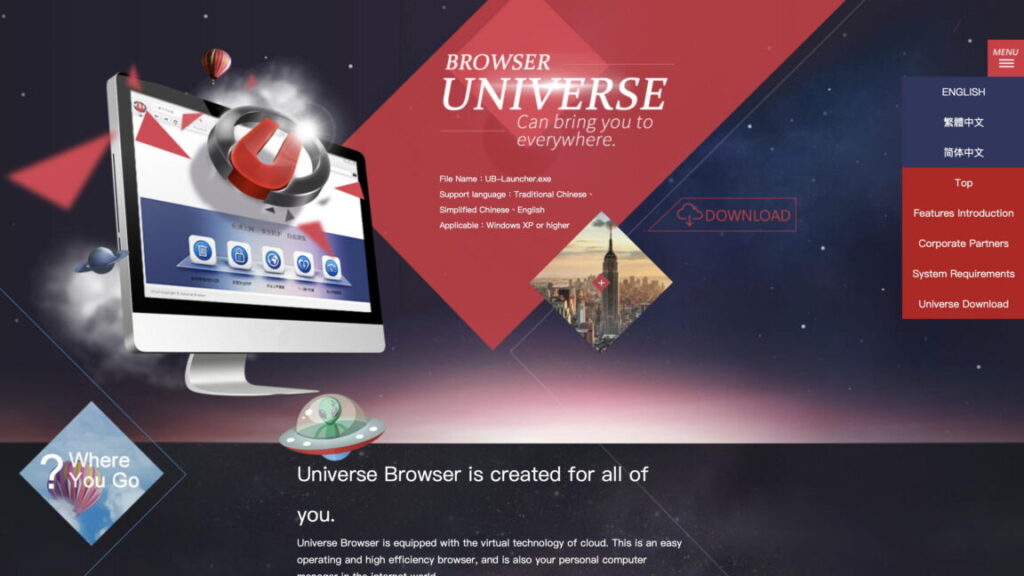
This browser claims “perfect privacies protection,” but it acts like malware
Researchers note links to Asia’s booming cybercrime and illegal gambling networks.
This looks like a 100 percent above-board product, right? Right? Credit: Ars Technica
The Universe Browser makes some big promises to its potential users. Its online advertisements claim it’s the “fastest browser,” that people using it will “avoid privacy leaks” and that the software will help “keep you away from danger.” However, everything likely isn’t as it seems.
The browser, which is linked to Chinese online gambling websites and is thought to have been downloaded millions of times, actually routes all Internet traffic through servers in China and “covertly installs several programs that run silently in the background,” according to new findings from network security company Infoblox. The researchers say the “hidden” elements include features similar to malware—including “key logging, surreptitious connections,” and changing a device’s network connections.
Perhaps most significantly, the Infoblox researchers who collaborated with the United Nations Office on Drugs and Crime (UNODC) on the work, found links between the browser’s operation and Southeast Asia’s sprawling, multibillion-dollar cybercrime ecosystem, which has connections to money-laundering, illegal online gambling, human trafficking, and scam operations that use forced labor. The browser itself, the researchers says, is directly linked to a network around major online gambling company BBIN, which the researchers have labeled a threat group they call Vault Viper.
The researchers say the discovery of the browser—plus its suspicious and risky behavior—indicates that criminals in the region are becoming increasingly sophisticated. “These criminal groups, particularly Chinese organized crimes syndicates, are increasingly diversifying and evolving into cyber enabled fraud, pig butchering, impersonation, scams, that whole ecosystem,” says John Wojcik, a senior threat researcher at Infoblox, who also worked on the project when he was a staff member at the UNODC.
“They’re going to continue to double down, reinvest profits, develop new capabilities,” Wojcik says. “The threat is ultimately becoming more serious and concerning, and this is one example of where we see that.”
Under the hood
The Universe Browser was first spotted—and mentioned by name—by Infoblox and UNODC at the start of this year when they began unpacking the digital systems around an online casino operation based in Cambodia, which was previously raided by law enforcement officials. Infoblox, which specializes in domain name system (DNS) management and security, detected a unique DNS fingerprint from those systems that they linked to Vault Viper, making it possible for the researchers to trace and map websites and infrastructure linked to the group.
Tens of thousands of web domains, plus various command-and-control infrastructure and registered companies, are linked to Vault Viper activity, Infoblox researchers say in a report shared with WIRED. They also say they examined hundreds of pages of corporate documents, legal records, and court filings with links to BBIN or other subsidiaries. Time and time again, they came across the Universe Browser online.
“We haven’t seen the Universe Browser advertised outside of the domains Vault Viper controls,” says Maël Le Touz, a threat researcher at Infoblox. The Infoblox report says the browser was “specifically” designed to help people in Asia—where online gambling is largely illegal—bypass restrictions. “Each of the casino websites they operate seem to contain a link and advertisement to it,” Le Touz says.
The Universe Browser itself is mostly offered for direct download from these casino websites—often being linked at the bottom of the websites, next to the logo of BBIN. There are desktop versions available for Windows, as well as an app version in Apple’s App Store. And while it is not in Google’s Play Store, there are Android APK files that allow the app to be directly installed on Android phones. The researchers say multiple parts of the Universe Browser and the code for its apps reference BBIN, and other technical details also reference the company.
The researchers reverse-engineered the Windows version of the browser. They say that while they have been unable to “verify malicious intent,” elements of the browser that they uncovered include many features that are similar to those found malware and tries to evade detection by antivirus tools. When the browser is launched, it “immediately” checks for the user’s location, language, and whether it is running in a virtual machine. The app also installs two browser extensions: one of which can allow screenshots to be uploaded to domains linked to the browser.
While online gambling in China is largely illegal, the country also runs some of the world’s strictest online censorship operations and has taken action against illegal gambling rings. While the browser may most often be being used by those trying to take part in illegal gambling, it also puts their data at risk, the researchers say. “In the hands of a malicious actor—a Triad for example—this browser would serve as the perfect tool to identify wealthy players and obtain access to their machine,” the Infoblox report says.
Beyond connecting to China, running key logging, and other programs that run in the background, Infoblox’s report also says multiple functions have been disabled. “The right click, settings access and developer tools, for instance, have all been removed, while the browser itself is run with several flags disabling major security features including sandboxing, and the removal of legacy SSL protocols, greatly increasing risk when compared with typical mainstream browsers,” the company’s report says. (SSL, also known as Secure Sockets Layer, is a historic type of web encryption that protected some data transfers.)
It is unclear whether these same suspicious behaviors are present in the iOS and Android versions of the app. A Google spokesperson says the company is looking into the app and confirmed it was not available through its Google Play store. Apple did not respond to requests for comment about the app.
Connect the dots
The web infrastructure around the Universe Browser led the researchers back to BBIN, a company that has existed since 1999. While it was originally founded in Taiwan, the company now has a large base in the Philippines.
BBIN, which also goes by the name Baoying Group and has multiple subsidies, describes itself as a “leading” supplier of iGaming software in Asia. A UNODC report from April, which links BBIN to the Universe Browser but does not formally name the company as Vault Viper, says the firm runs several hotels and casinos in Southeast Asia as well as providing “one of the largest and most successful” iGaming platforms in the region. Over the last decade, BBIN has sponsored or partnered with multiple major European soccer teams, such as Spain’s Atlético de Madrid, Germany’s Borussia Dortmund, and Dutch team AFC Ajax.
In recent years, multiple football clubs in England’s Premier League have faced scrutiny over sponsorship by Asian gambling companies—including by TGP Europe, which was owned by Alvin Chau, the chairman and founder of SunCity Group, who was sentenced in January 2023 to 18 years in prison after being found guilty of running illegal gambling operations. TGP Europe left the UK earlier this year after being fined by the country’s gambling regulator. Atlético Madrid, Borussia Dortmund, and AFC Ajax did not respond to WIRED requests for comment.
The iGaming industry develops online gambling software, such as virtual poker or other online casino games, that can easily be played on the web or on phones. “BBIN Baoying is officially an online casino game developer or ‘white label’ online casino platform, meaning it outsources its online gambling technology to other sites,” says Lindsey Kennedy, research director at The EyeWitness Project, which investigates corruption and organized crime. “The only languages it offers are Korean, Japanese, and Chinese, which isn’t a great sign as online gambling is either banned or heavily restricted in all three countries.”
“Baoying and BBIN are what I would call a multi-billion dollar gray-area international conglomerate with deep criminal connections, backstopping and providing services to online gambling businesses, scams and cybercrime actors,” alleges Jeremy Douglas, chief of staff at the UNODC and its former regional representative for Southeast Asia. “Aside from what has been estimated at a two-thirds ownership by Alvin Chau of SunCity—arguably the biggest money launderer in the history of Asia—law enforcement partners have documented direct connections with Triad groups including the Bamboo Union, Four Seas, Tian Dao,” Douglas says of BBIN. (When Chau was sentenced in January 2023, court documents pointed to him allegedly owning a 66.67 percent share of Baoying).
BBIN did not respond to multiple requests for comment from WIRED. The firm’s primary contact email address it lists on its website bounced back, while questions sent to another email address and online contact forms, plus attempts to contact two alleged staff members on LinkedIn were not answered by the time of publication. A company Telegram account pointed WIRED to one of the contact forms that did not provide any answers.
The Presidential Anti-Organized Crime Commission (PAOCC) in the Philippines, which tackles organized and international crimes, did not respond to a request for comment from WIRED about BBIN.
Over the last decade, online crime in Southeast Asia has massively surged, driven partially by illegal online gambling and also a series of scam compoundsthat have been set up across Myanmar, Laos, and Cambodia. Hundreds of thousands of people from more than 60 countries have been tricked into working in these compounds, where they operate scams day and night, stealing billions of dollars from people around the world.
“Scam parks and compounds across the region generally host both online gambling and online scam operations, and the methodology used to lure individuals into opening online gambling accounts parallels that associated with pig-butchering scams,” says Jason Tower, a senior expert at the Global Initiative Against Transnational Organized Crime.
Last week, US law enforcement seized $15 billion in Bitcoin from one giant Cambodian organization, which publicly dealt in real estate but allegedly ran scam facilities in “secret.” One of the sanctioned entities, the Jin Bei Group in Cambodia, which US authorities accused of operating a series of scam compounds, also shows links to BBIN’s technology, Tower says. “There are multiple Telegram groups and casino websites indicating that BBIN partners with multiple entities inside the Jinbei casino,” Tower says, adding that one group on Telegram “posts daily advertisements indicating an official partnership between Jinbei and BBIN.”
Over recent years, multiple government press releases and news reports fromcountries including China and Taiwan, have alleged how BBIN’s technology has been used within illegal gambling operations and linked to cybercrime. “There are hundreds of Telegram posts aggressively advertising various illegal Chinese facing gambling sites that say they either are, or are built on, BBIN/Baoying technology, many of them by individuals claiming to operate out of scam and illegal gambling compounds, or as part of the highly illegal, trafficking-driven industry in Cambodia and Northern Myanmar,” says Kennedy from The EyeWitness Project.
While the Universe Browser has most likely been downloaded by those accessing Chinese-language gambling websites, researchers say that its development indicates how pivotal and lucrative illegal online gambling operations are and exposing their links to scamming efforts that operate across the world. “As these operations continue to scale and diversify, they are marked by growing technical expertise, professionalization, operational resilience, and the ability to function under the radar with very limited scrutiny and oversight,” Infoblox’s report concludes.
This story originally appeared on wired.com.
This browser claims “perfect privacies protection,” but it acts like malware Read More »