The curious rise of giant tablets on wheels
Over the past few years, LG has set off a strange tech trend that’s been rolling onto devices sold across Amazon and other online electronics retailers.
In 2022, the company launched the StanbyME, which is essentially a $1,000 27-inch tablet running LG’s smart TV operating system (OS), webOS, but lacking a tuner. LG’s press release announcing the device described it as a “wireless private TV screen with a built-in battery” that is easily portable and ideal for watching shows and movies, in addition to “video conferencing with family and coworkers and viewing online lectures.”
Today, the StanbyME competes against a slew of similar devices, including some from Samsung, but mostly from smaller brands and running Android.
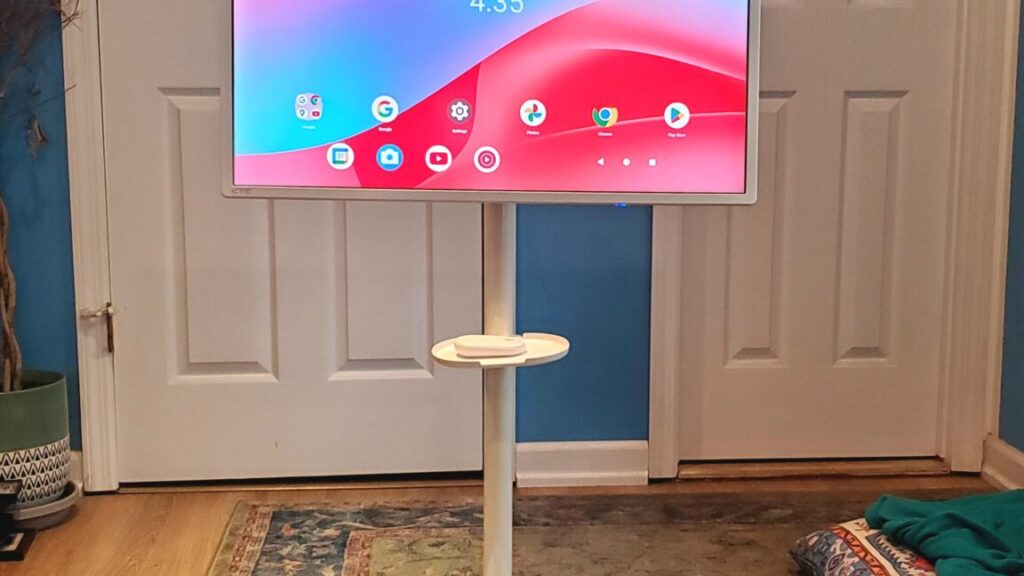
I’ve had one of these devices, the KTC MegPad 32-inch Android Tablet (A32Q7 Pro), rolling around my home for a few weeks, and I’m left curious about what’s driving the growth of StanbyME-like devices, which are noticeably niche and expensive. I’m also uncertain whether these hybrid devices have an ongoing place in a consumer tech world already inundated with big-screen TVs, small-screen tablets, and beloved laptops.
Hands-on
Unlike LG’s StanbyME, KTC’s device doesn’t run a smart TV OS. Instead, it’s a 32-inch Android 13 tablet. Still, KTC heavily markets the MegPad’s ability to serve as streaming hardware, and that’s one of the best uses I found for it.
A big ol’ tablet on wheels. Scharon Harding
Treating the MegPad like a smart TV on wheels meant I could have a living-room-like experience in more places throughout my home. I could watch TV in bed with a more visible screen set at a more comfortable distance than what I’d achieve with a laptop or tablet. It also meant flexibility. I don’t like having a permanent TV in my room (how would I ever get out of bed?), so I appreciated the ability to roll the MegPad out of my room or twist it so that the screen faced away from me.
The MegPad is also a diplomatic solution for homes with limited TVs or computers. This could be helpful for homes with kids with varied interests or in my home, where a speedy, 55-inch TV in the living room is the best screen available by far. I was able to let my partner take the big screen for gaming and still hang out nearby while streaming on the MegPad. I don’t have a central coffee table in my living room, but the mobile tablet enabled me to watch shows without a device weighing down my lap or making me connect a wireless speaker for better volume.
KTC’s device also has a helpful leg-up over LG’s StanbyME via its HDMI port, which makes the MegPad work like a regular monitor. Determining where to safely rest a device tethered to this mobile machine is something you’ll have to figure out on your own, though.
The port selection on the panel’s backside. Credit: Scharon Harding
Compared to the TV mounted on my living room wall, the MegPad is much easier to move from room to room, but it’s easy to overestimate how seamless transporting it is. Yes, it’s on a set of five 360-degree wheels, but the wheels don’t lock, and the device weighs 40.3 pounds, per its Amazon listing. That means I had to exert a decent amount of effort to move it over floor transition strips, across uneven floors, and from hardwood to carpet.
The charging port and power button are on the stand’s base. Credit: Scharon Harding
A fully rotating screen, however, makes up for some of my mobility complaints and diversifies the MegPad’s potential uses. Besides streaming, for example, the MegPad was great for watching yoga videos online, (which calls for viewing the screen from different heights and positions). It also proved to be an ideal setup for creating a large, print-out collage, which included a lot of dragging, dropping, and cropping of images.
How the MegPad moves. Credit: KTC
Not a real TV
You can do a lot with a sizeable Android tablet. But with TV and movie watching being some of the most obvious uses, it’s important to note that neither the MegPad nor any of its rollable rivals are real TVs.
For one, there’s no tuner, though in the streaming world, that matters less to many of today’s TV viewers.
Further, the MegPad, like many StanbyME-like devices, uses Android 13, which doesn’t require paying vendor licensing fees like built-for smart TV OSes, such as Android TV/Google TV and webOS, would. There are some benefits to that, though.
To start, Android 13 doesn’t have the integrated ads that Android TV or the Google TV interface does. Google claims that the Google TV platform doesn’t use automatic content recognition (ACR), but as Consumer Reports has noted, Google collects “data from TVs that use its smart TV platform—and there’s no opting out of Google’s policies during setup if you want smart TV functionality.” Further, Google may combine that data with user data from third parties for advertising purposes. A spokesperson for KTC confirmed to me that the MegPad doesn’t use ACR.
As a tablet, the MegPad is compatible with more apps, many of which aren’t supported by Google TVs, like Google Sheets, Microsoft Word, Reddit, and Signal.
Android tablets are also more appropriate for storing documents, photos, and other files than smart TVs are. Although it’s likely less roomy than your PC, the MegPad has 128GB of internal storage.
But since this is an Android tablet and not a Google TV, there are no integrated channels and no live-TV-only option, which stops the device from collecting diagnostic information. Google TV would also include a more streaming-friendly user interface and the ability to watch content from different streaming providers without switching apps.
Further differing from LG’s StanbyME and real TVs, the MegPad doesn’t include a traditional remote. The tablet comes with a basic Bluetooth mouse, but due to the tablet’s portability, I frequently used the tablet without a flat surface within arm’s reach available for comfortable mouse control. The touchscreen is reliable, but gestures can be cumbersome on a tablet this large, and the display was often out of my hand’s reach.
The tablet comes with this mouse and removable mouse stand. Credit: Scharon Harding
The new portable TV?
With TVs getting larger and people turning to portable gadgets like phones and laptops for TV watching, true portable TVs have become a rarity. Demand for a small device dedicated to on-the-go TV viewing has dropped significantly since the last century. Meanwhile, fabs and supply chains are built around monitor and TV-sized displays, making it difficult to incorporate some of the most desirable display technologies, like OLED, into smaller-sized panels with competitive prices.
As a result, devices like the MegPad and Amazon’s Echo Show have become the new de facto stand-ins for portable TVs, even though they’re not true TV sets. Even LG’s StanbyME Go, a 27-inch webOS-powered display packed into a briefcase, is a far cry from what most of us would traditionally consider a portable TV.
LG’s StanbyMe GO.
Credit: LG
LG’s StanbyMe GO. Credit: LG
Again, these tablets have more versatility than the small, telescoping-antenna-equipped boxes you used to stick on your kitchen counter or hand to a hyper kid during road trips. But they also require a reliance on Big Tech software and all the privacy and ethical implications that come with that.
You don’t see many of these anymore. From left to right: Casio EV 570, Sony Watchman, and Casio EV 660. Credit: Richard Derk/Los Angeles Times via Getty Images
KTC also sees the MegPad’s appeal as a pseudo-TV. The MegPad’s product page emphasizes users’ ability to “watch favorite shows/movies directly—no PC needed” and to “stream Netflix [and] YouTube… more effortlessly on your smart TV.” Its Amazon product page also promotes the keywords “portable TV,” “rolling TV,” “mobile TV,” and “standing TV.” This is all despite the MegPad not technically being a true TV.
“KTC defines the MegPad A32Q7Pro as a portable, smart, touchscreen monitor,” KTC’s spokesperson told me. “It combines key traits of a smart display and a large-screen tablet. While it shares some features with smart TVs, tablets, and monitors, it doesn’t fully belong to any single traditional category. It’s a hybrid device designed to bridge those use cases.”
Android tablets on wheels
Many devices like the MegPad represent a push for more Android-powered, non-Google devices that has been buoyed by a program that Google launched in 2022, the Enterprise Devices Licensing Agreement (EDLA).
As explained by partners like BenQ, EDLA is a way for third parties to incorporate Google Mobile Services (GMS), which are Google’s most commonly used apps and APIs bundled for use across different types of devices. GMS apps include popular software like Google Drive, Gmail, the Google Play Store, and YouTube.
“Previously, GMS was only officially available for smartphones, tablets, TVs, and wearables. Under the new EDLA, the list of devices eligible for GMS certification has now been expanded to include enterprise solutions such as smart boards,” a blog from BenQ, which has EDLA-certified smart displays, reads.
Since 2022, (the year LG’s StanbyME launched), there has been an uptick in non-Google devices with this EDLA certification. One of the categories taking advantage of the newer program is tablets on wheels, like the MegPad and similar options from Kefeya, Apolosign, Innocn, and DuraPro.
Demonstrating the marketing value of EDLA certification, the MegPad’s product page reads: “Google EDLA certification provides secure, direct access to Google services and the Google Play Store with regular updates, offering greater stability and data protection than open app ecosystems with unverified apps.”
Most EDLA-certified devices seem to be interactive displays used for education. With EDLA certification, devices like the MegPad may also draw the attention of educators or even businesses. Meanwhile, Google is happy to hand out EDLA certifications, as they can drive Android adoption, giving Google more data and access to customers outside of the typical Android devices, such as phones. Products like the MegPad can also be easier to shop with (Google loves when people use its offerings to shop) than Android devices with smaller screens.
Who’s this for?
I’ve been fascinated by the MegPad and similar devices because they introduce a unique approach to streaming, web browsing, and productivity. But ultimately, they’re hard to recommend when there are other personal gadgets that are more affordable and often take up less space.
I had fun with the MegPad and appreciated the flexibility it offered, especially in my smaller NYC home. There are some specific use cases where products like this could excel, like if you want to bring a computer or screen into a room that doesn’t always need one. It was also helpful as an entertainment center for my father post-surgery, when he primarily had to lie on one side in bed.
Overall, the growing presence of devices like the MegPad underscores a confluence occurring between smart TVs, tablets, monitors, and smart displays. With software being forced into more types of displays, often in the interest of gathering more user data, it’s an interesting time to consider what you want from your next screen—be it computing power, a certain size, the omission or inclusion of web connectivity, and mobility.
It appears that the MegPad and similar tablets are trying to take advantage of the attention that LG garners when launching distinctive devices like its StanbyME line. Besides a StanbyME lookalike, Apolosign also makes a device similar to the StanbyME Go.
Apolosign’s PackGo is very similar to LG’s StanbyME Go. Credit: Apolosign
Three years after LG made TV-esque devices on wheels a talking point, more brands are trying to roll into the market. That includes LG’s best TV frenemy, Samsung, which has been using the form factor in limited geographies to drive sales of “smart monitors.”
Tech brands have ulterior motives for pushing this newer form factor that go beyond filling a gap in consumer gadgets. But if a large tablet or small smart display with wheels fits your needs, the options are there, and they should meet most expectations.
The curious rise of giant tablets on wheels Read More »